Given all the breaches, hacks, and DDoS attacks that have occurred lately, it reminded me of how vulnerable we truly are. Not only in the businesses we deal with but right here in our own homes. Add to this the onslaught of devices that we are connecting to our homes from companies who could care less about, or know nothing about building in the proper internet security, and you have a recipe for concern. Given all these variables, we now have the largest uncontrolled market we have ever seen. I am not trying to paint a picture of gloom and doom as technology does enhance our lives in so many ways, but rather remind all of us to take precautions even if it means a bit more work or expense as in the long run, it will pay off. I have attempted to put together a short list of some suggested practices that have worked for me to maximize your security and safety. Remember, most security issues come from inside our walls and we should do everything we can to control what happens inside our homes.
Suggested Best Practices
- Disable UPnP
Many issues can arise from the use of UPnP. Yes, it is convenient but it does open you up to extra vulnerabilities. Not because it is a particularly bad standard, but rather how each company chooses to deploy it not to mention the fact that it can open numerous ports without your knowledge. Take the average NAS like QNAP or Synology. If you use UPnP with those devices, they will open almost a dozen ports in your router for the various apps as each needs its own port to operate correctly. It is best to stay away from UPnP and configure only the needed ports in your router yourself.
- Mind the devices that are connected to your network.
You need to consider what functionality you need from a device. Just because you can connect your TV, fridge, or appliance to the internet, doesn’t mean you want to. At least not before you completely understand what and how it will connect to. Take a good look at the features it offers and learn exactly how it is configured before you connect. It is your network and you need to know how it is going to be used. If you are not sure, do some searching for any security concerns.
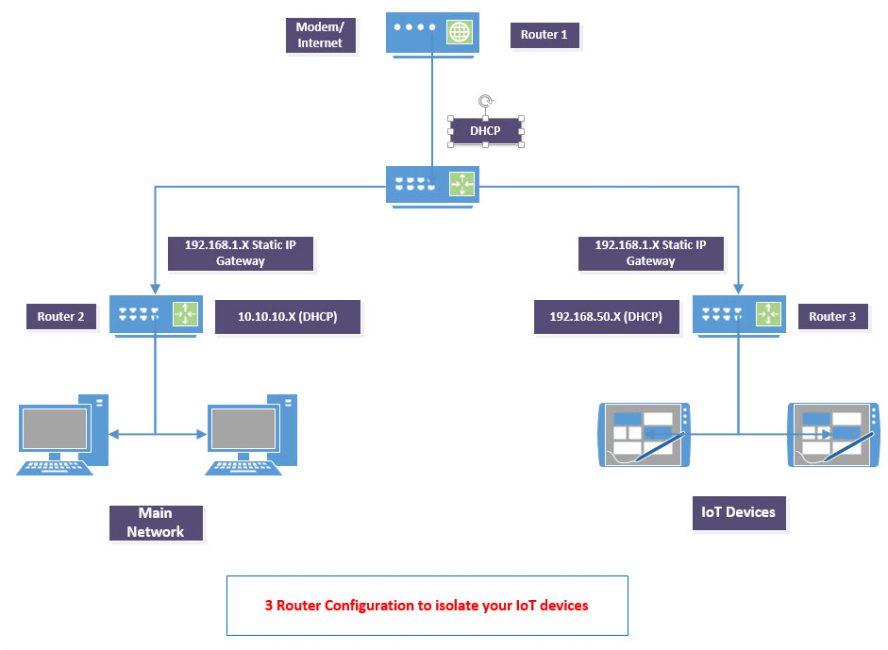
- Create a separate IoT network
- Best practices with IoT devices is separation. There are many ways you can do this but the main goal is to completely isolate your IoT devices from your network and other files. If your router supports it, create two separate networks with no crossover to your main network, or search for ways to use multiple low cost routers to accomplish the same thing.
- Use a VPN. For items, such as IP cameras, NVRs, and other items that you would like to access from outside, you can deploy a free VPN solution. By doing this it allows you disable all the port forwarding and funnel everything through one connection. For access to IoT devices from outside your home, using a VPN is a good alternative and is much safer. Many routers, NAS, and UTM’s today have VPN built in that provide you a free and effective way to hook up to your network.
- Update your devices
Just like your OS, these devices need frequent updates. Often security flaws in these devices are patched, however most of the updates are not automatic so you must take matters into your own hands. Regularly check and patch the devices such as IP cameras, hubs, and routers that do not have auto updates.
- Don’t use a device that does not allow you to change credentials
There are some low-cost devices out there that come pre-programmed with URL’s or fixed user names/passwords, or worse, no credentials. These are not worth your time and you should avoid putting them on your network especially if you do not have your networks yet separated. On the deceives that you can change the credentials, remember to always change the default login with something secure.
- Use a strong firewall
I know it can be painful and often there is a learning curve, but use a decent router/firewall that allows you more control. Though it may take you longer to setup and you might smack your head on the wall a few times with getting everything right, in the end the effort will be worthwhile and you will have better understanding of how your your firewall and network are configured.
- Investigate cloud services and limit the number of them
Let’s face it, we have a ton of accounts and many are for devices. An account, or several of them, for IP cameras, off the shelf routers, and home automation stuff just to name a few. It is best practice to see if is possible to minimize that. If you buy 3 types of IP cameras for example, try to use something that controls all the cameras locally such as Blue Iris, iSpy, Synology, or a QNAP and funnel everything through one account or preferably use your VPN account.
- Use unique and strong passwords for each device
It’s very important to pick strong passwords, but you must also make sure that you pick a different password for every device. Reusing passwords is never a good idea. Use a password manager to keep track of all your passwords.
- Track what is happening on your network.
If you have a higher end firewall, you will be able to log the traffic on your network, but if you have a traditional router with little to no ability to log or filter, then consider using something like OpenDNS. You can start with the free version and test it out, then for $20/Year you can upgrade to better filter content. It is always good to keep an eye on what is going on with incoming and outgoing traffic to help control and identify problems.
Comment on IOT Devices
A few closing words on IoT devices as this has quickly become a large segment of the connected market. Depending on how you classify the Internet of things, there are thousands upon thousands of devices that fall into this category. Things like home automation hubs, irrigation controllers, security cameras, thermostats, appliances, smart TVs, and media players just to name a few. These have become an integral part our day to day lives. The secret now is to make sure they are as secure as possible and they don’t become the weakest link in our security. It is important to remember that due to a high variety of manufacturers, the potential for lousy security is very high and it is up to you to keep these devices current.
If you are heavy into IoT devices, you will want to explore the options for network separation including the use of separate Wi-Fi access points. There are many variations of how to use multiple routers or a low cost managed switch to accomplish this, but my preferred way is to get a router that lets you do that out of the box as there are less hops and it is slightly easier to configure. If you do some research you should be able to find a solution that works for you without spending allot of money. I have been using separate networks for years now (See My Network) though I originally did it for slightly different reasons. In the end, the main point is whatever solution you use, you should keep your critical files separated from your IoT devices.