If you follow security news at all you will already know that IOT is becoming more and more insecure. Between the known vulnerabilities and the fact that you may not receive any patches for your device, to the sheer number and variety of devices makes is virtually impossible to keep current. I would guess that in the average home today there are at a minimum of six+ IOT devices and some will never get patched. Things like smart lights, Amazon Echo, Phillips Hue, Cable/Satelite receivers, smart TVs, and streaming boxes just to name a few. To make things worse, many of these use chipsets that are made by a third party making it even more challenging to keep things patched. The one thing we can all do to protect ourselves is to keep these devices segregated so they can’t contaminate our home networks. Below is a video that demonstrates how to use an inexpensive Edgerouter to create an IOT network. In addition to the video, the instructions are replicated on this post to help you get things set up.
Instructions
- Start by running the WAN + 2 LAN 2 Wizard. Except for the firewall rules, the wizard takes care of most of the configuration
- Leave eth0 at default
- Uncheck “Only Use One LAN”
- Configure each port
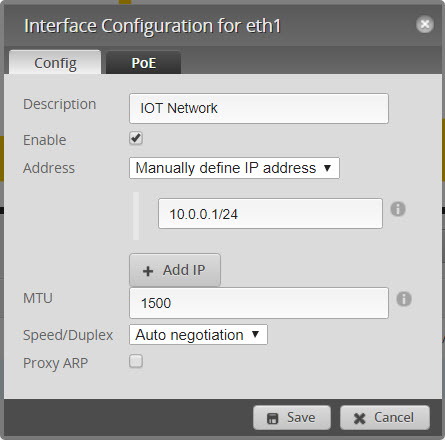
- eth1 (IOT) with 10.0.0.1/24,
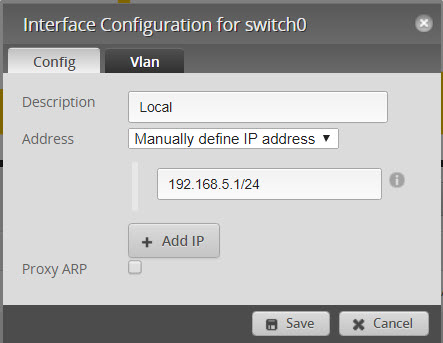
- eth2 (Main Devices) with 192.168.5.1/24
- Enable DHCP on both eth1 and eth2
- Create a New Password
- Apply/save your changes
- Reboot (you will need to change your network IP settings back to Auto so that you can access the Web UI again.
Firewall/Settings
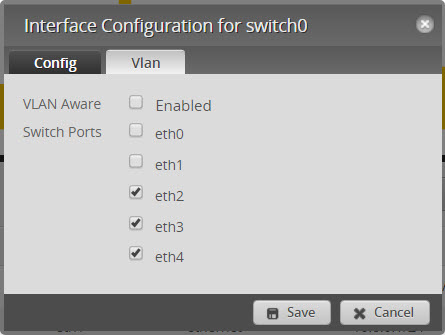
- Configure Swith0 to remove eth1
- Click on VLAN and verify that eth1 is unchecked
- Configure eth1
- IP address (10.0.0.1) and description (IOT Net)
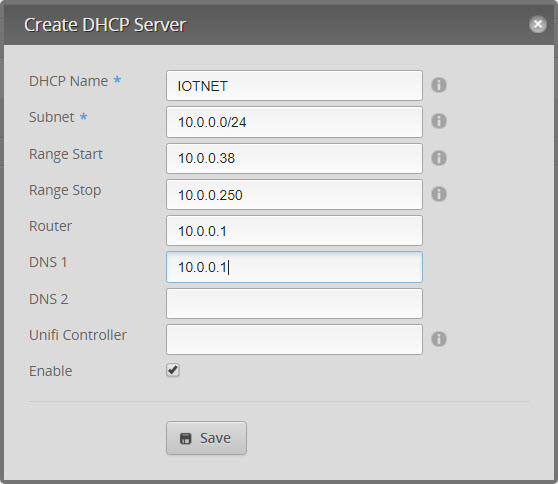
- Go to Services, DHCP (This is not required if you ran WAN+@LAN2 wizard)
- Add DHCP server and click on Save
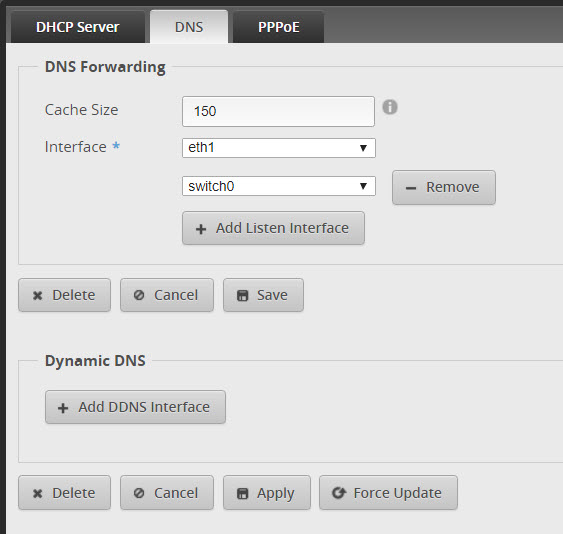
- Go to Services and click the DNS tab
- Go to Firewall/NAT
- Click on Firewall/NAT Groups
- Click on ADD Group
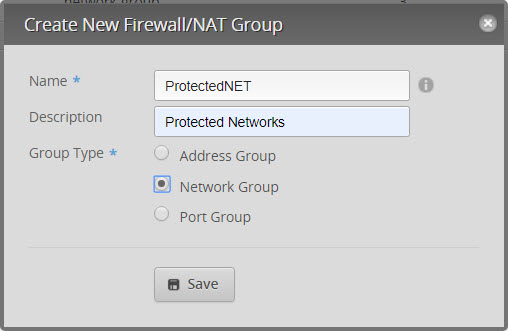
- Go to Firewall and create a new Firewall group
- Add Name and Description and click on SAVE
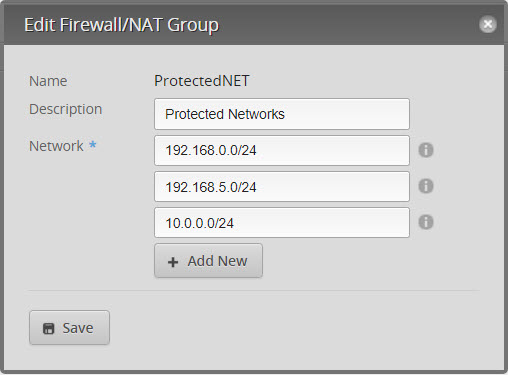
- Click on “Actions” and select Config the Network group
- Add all the networks
- Go to Firewall Policies
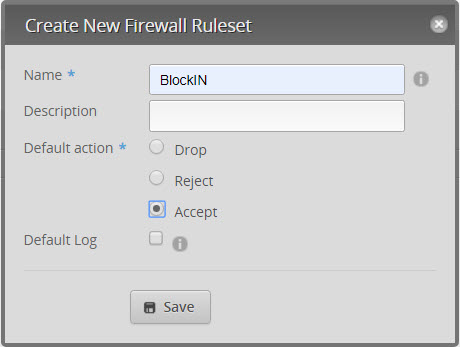
- Add a rule set called BlockIN (Name and optional Description) and SAVE
- Edit the ruleset
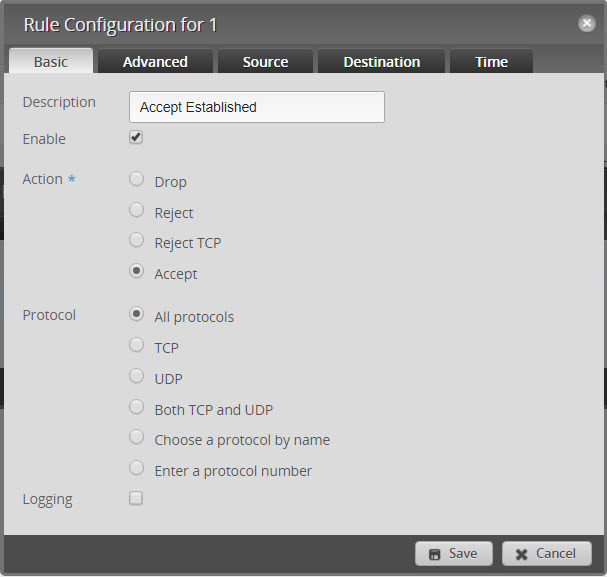
- Add New Rule called Accept Established
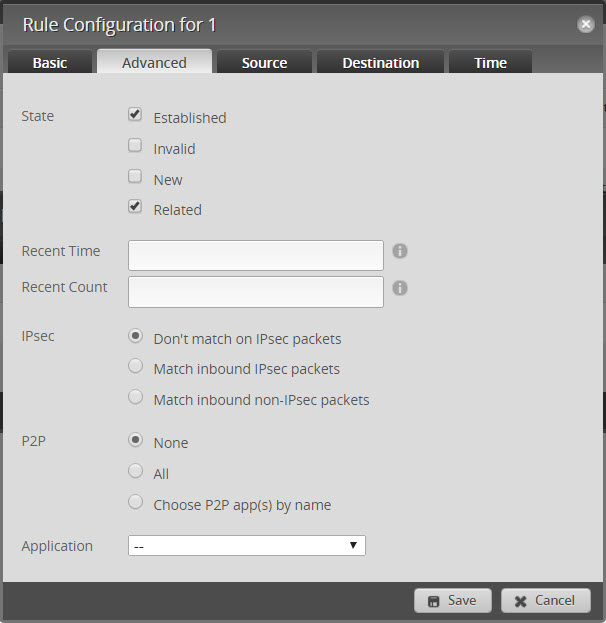
- Click on “Advanced” and select Established and Related
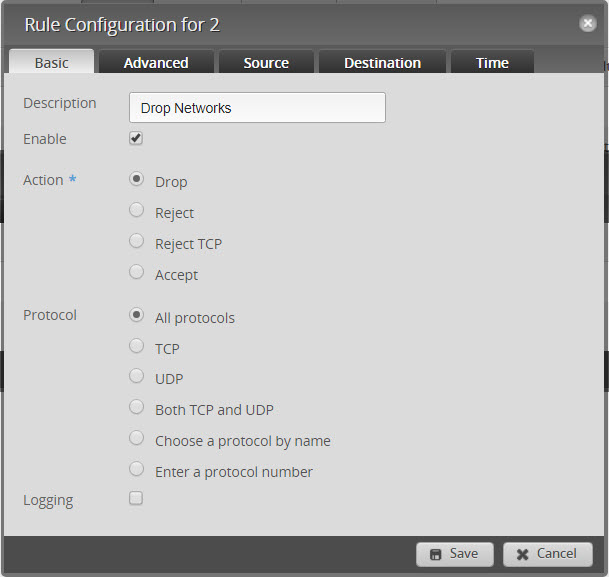
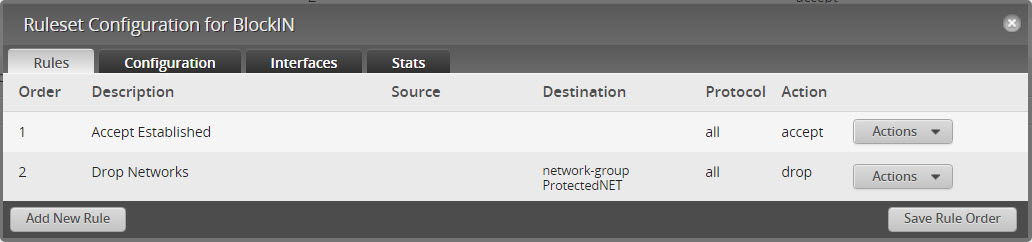
- Create another new rule and call it “Drop Protected Networks”
- Action = Drop, Protocols “All”
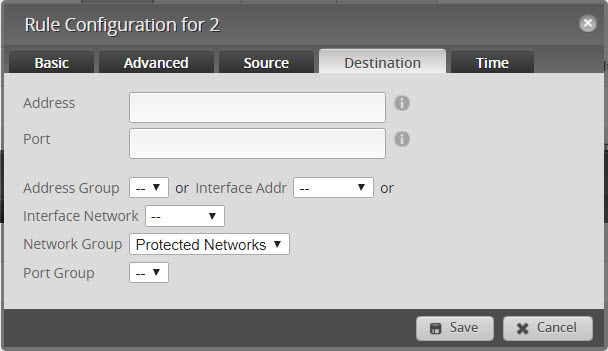
- Go to Destination and select “Protected Networks”
- Your rules should now look like this
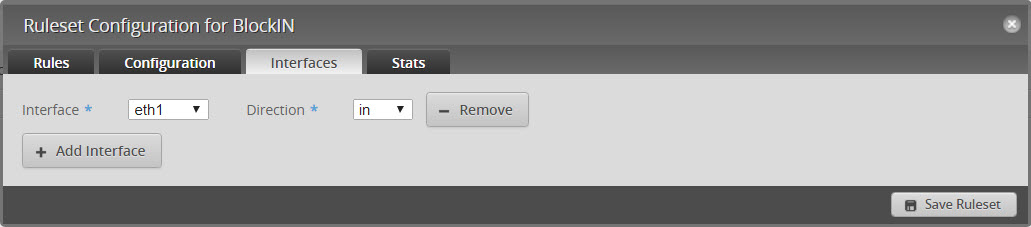
- Click on “Interfaces” and assign interfaces and direction to rule
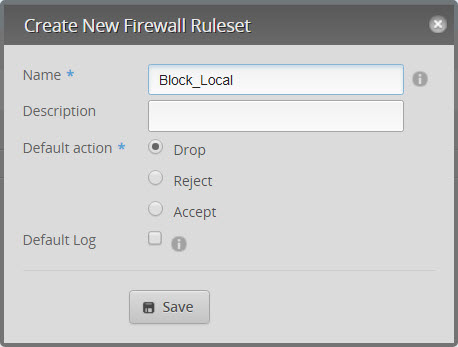
- Add another rule set called block_ local (to block IOT from accessing services on the main LAN). Default is drop and then hit SAVE.
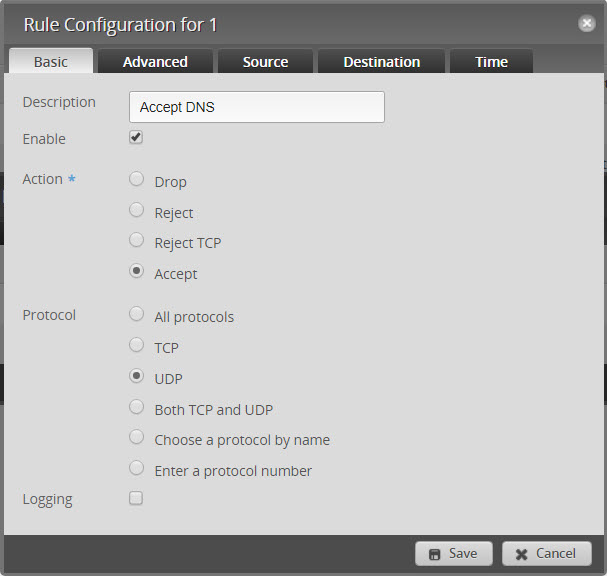
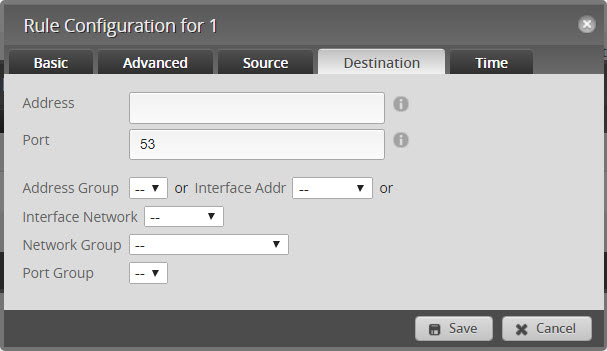
- Edit the ruleset and Add New Rule Called Accept DNS
- The default will be “Accept” and “UDP”
- Click on the “Destination”
- Set port to 53
- Click Save
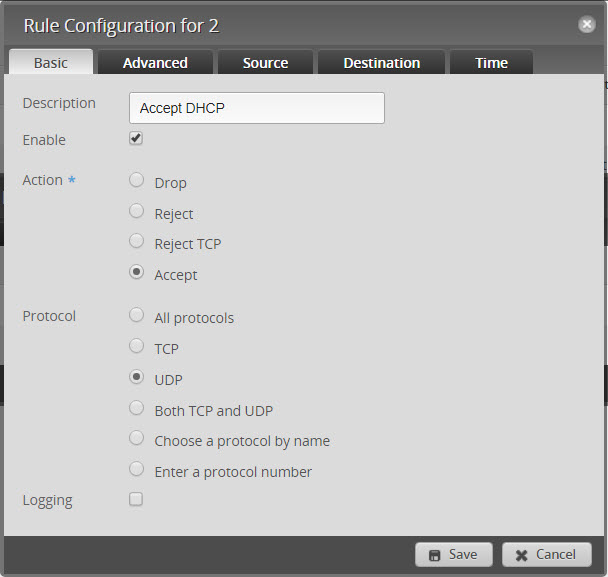
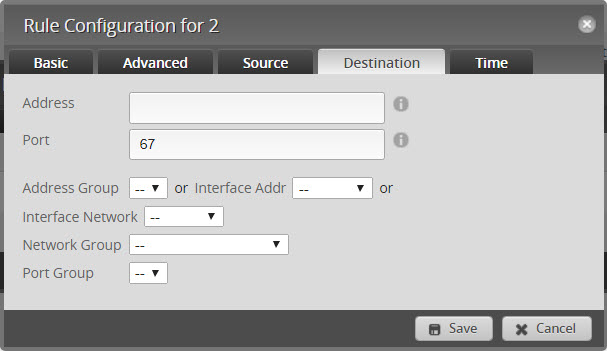
- Add a second new rule called “Accept DHCP”
- Click on “Destination”
- Set to Port 67 and click on SAVE
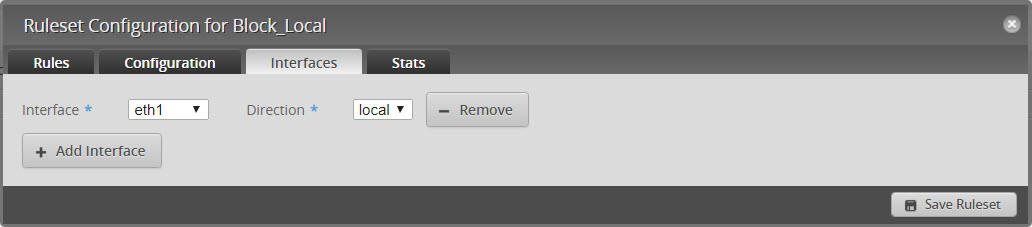
- Edit Ruleset and click on “Interfaces”
- Set Interface to eth1 and Direction to LOCAL and click on “Save Ruleset”
Should now be able to get an IP with isolation
- Test to see if you can ping each network
- Make sure that DHCP works on both Networks
- Internet connection (both networks)
- From the Main Devices Network (or whatever you called it) at a minimum perform a “ping” test
- Main to IOT
- Main to First Firewall
- Access to the Web UI
- From the IOT Network (or whatever you called it) at a minimum perform a “ping” test
- At a minimum perform a “ping” test
- IOT to Main (if you are using a primary router)
- IOT to Main Devices Network
- Test that you can not access the Web UI for the edge router
[/fusion_text][/fusion_builder_column][/fusion_builder_row][/fusion_builder_container]


Great tutorial, do you have also the same to working with Sophos XG firewall to Securing the network from IOT?
Yes, I sure do. I use several VLANs as well as a segregated network on Sophos.