As we become more security conscious, the idea of throwing a bunch of IOT devices and creating guest WiFi connections should scare the heck out of us. As we deploy more and more insecure IOT devices, there is an increased risk for potential problems. As it is not always practical to create separate physical networks, one great option is to use your Sophos Firewall (or any comparable firewall) and your VLAN aware access point to create one or more VLANs to minimize the risk and make your home or business more secure. At a minimum, you should create a VLAN for your IOT devices but I would also recommend you creating one for all your guest devices as well even if you control who accesses your network. The reason I think it is more important to create a segregated IOT network is that most access points today at least have a guest function which segments the network. Creating a VLAN on your guest network is still important but it far more important to deal with the wild, wild west of IOT. Whether you use home automation, media streaming devices, cable boxes, TVs, or the latest wifi enabled device, you need to protect your home or business from these rogue devices. Many of these devices are not patched and can be vulnerable to attacks making your network a possible attack point.
In the video and article below I will walk you through creating an IOT/Guest VLAN using Sophos XG and a Unify AP AC Pro access point/controller. For more information on the UniFy AC Pro, see my post here. You can also use any VLAN aware access point to accomplish the same thing. Refer to your MFG documentation to complete the last step of this process.
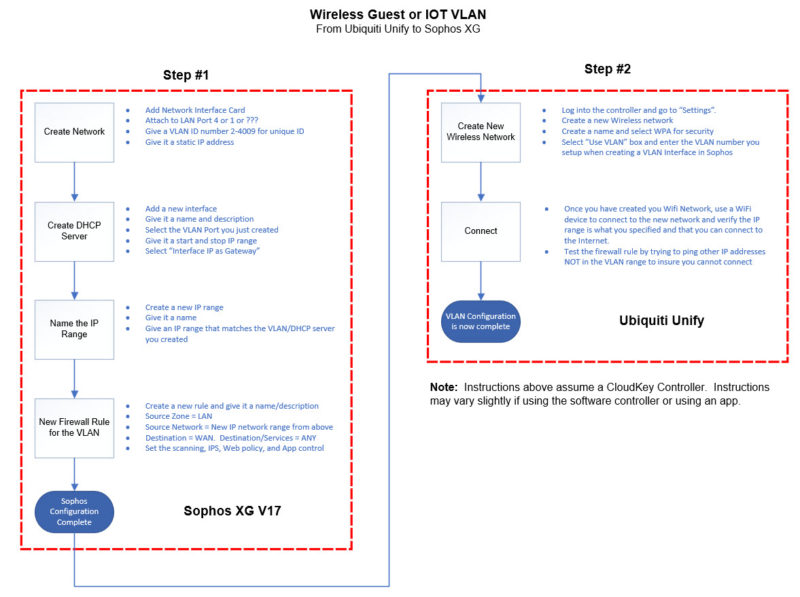
As with most things in Sophos XG, there are a few steps involved in creating a VLAN. Once you complete the first one and understand the concepts, creating additional VLANs is pretty easy. Conceptually, the entire process consists of creating a VLAN interface, creating a DHCP server, assigning an IP range, and creating a firewall rule to make it all work. The video will walk you through the process and the information below will hopefully serve as a guide for you to add more to your networks as your needs increase.
Sophos XG
Create Network
- From the “Network” section create a new interface. Select VLAN
- Bind it to your LAN port so that it is attached to the physical interface that your LAN is on
- Select LAN for the Zone
- Give it a VLAN number. You can use any number in between 2-4094, for example, 100
- Give a static IP that is different from your LAN. If you LAN is 192.168.1.1, then use something like 10.0.0.1 or 192.168.50.1
Create DHCP for New Network
- Click on DHCP and create a new DHCP server
- Give a Name
- Select the VLAN interface you created in the previous step (i.e. 100)
- Input the start and stop range. For example, if you used 10.0.0.1 for the static IP of your VLAN interface, then you could set a range of 10.0.0.50 – 10.0.0.100 as the DHCP range for you Guest or IOT network
- Select the option “Use Interface IP as Gateway” then save
Create and Name New IP range
- Go to the “Host and Services” tab and create a new IP host. This will be used to identify your new network
- Give a name such as “GuestVLAN” or “IOT Network”
- Select “IP Range” for the Type
- Input the range of the new VLAN network you created such as 10.0.0.1 to 10.0.0.254. This gives your new network an identity to be used in the firewall rule.
Create Firewall Rule
- From the Firewall section, create a new User/Network Rule. Give it a name and description
- For the Source:
- Zone = LAN
- Network = “Name of the new network” such as IOT Network or GuestVLAN
- For the Destination
- Zone = WAN
- Destination = ANY
- Services = ANY
- Select the scanning you want as well as the IPS, and filtering you need and save the rule
Unify Controller
Create New Wireless Network
- From the settings section for the controller, create a new wireless network
- Give a name, required security such as WPA, and type the desired security key
- Optionally if this is a guest network, select “Apply Guest Policy”
- Click on “Advanced” and select the “Use VLAN” option and type in the VLAN ID you created from above (i.e. 100). This tells wireless traffic to use your VLAN.
- Leave everything else as default
From here you should be able to attach a device to your new wireless network and it should give you an IP from the DHCP range you created in your Sophos Firewall. Your new VLAN network should now be isolated from your base LAN providing you with a higher level of security.
As a side note, you can create a firewall rule that gives one-way access to the IOT network for device management without giving permission for that network to communicate with your main network.